INFORMATION SECURITY POLICY
INFORMATION SECURITY POLICY
Last Updated: July 23, 2025 | Effective: July 23, 2025
Best Budz is a brand of TP Touch Down Solutions LLC
Contact: https://bestbudzonline.com/
Contents
Introduction
Information Security Policy
Network Security
Acceptable Use Policy
Protect Stored Data
Information Classification
Access to Sensitive Cardholder Data
Physical Security
Protect Data in Transit
Disposal of Stored Data
Security Awareness and Procedures
Credit Card (PCI) Security Incident Response Plan
Transfer of Sensitive Information Policy
User Access Management
Access Control Policy
Appendix A – Agreement to Comply Form
Appendix B – List of Devices
Appendix C – List of Third-Party Service Providers
Appendix D – Stand-Alone & P2PE POI Management Policy
Appendix E – eCommerce Configuration & Hardening Policy
1. Introduction
This Policy governs all aspects of information security for Best Budz and applies to employees, contractors, and vendors. Personnel must read the entire document and sign the acknowledgement form (Appendix A). Management reviews and updates the Policy at least annually or sooner if new security standards arise.
2. Information Security Policy
Best Budz processes sensitive information daily. Adequate safeguards protect account data—including cardholder data and customer privacy—to ensure regulatory compliance and support business continuity. Employees handling sensitive data shall:
Handle information according to its classification.
Limit personal use of company systems and avoid interference with job performance.
Acknowledge that Best Budz may monitor, access, review, audit, copy, store, or delete any electronic communications, equipment, systems, and network traffic.
Refrain from using company resources for offensive, discriminatory, defamatory, harassing, or illegal activities.
Protect sensitive account data, including cardholder information.
Keep passwords and accounts secure.
Obtain management approval before installing software, hardware, or establishing third-party connections.
Keep desks clear of sensitive data and lock computer screens when unattended.
Report information-security incidents immediately to the designated incident-response contact.
Complete annual security-awareness training.
3. Network Security
A high-level network diagram of the cardholder-data environment (CDE) is maintained and reviewed annually.
Approved Scanning Vendor (ASV) scans are performed quarterly (every 90–92 days) and evidence retained for 18 months.
For e-commerce, scans include any redirect/iFrame servers in scope.
4. Acceptable Use Policy
Employees must exercise good judgment regarding personal use of company assets.
Prevent unauthorized access to confidential information, including cardholder data.
Keep passwords secure and never share accounts.
All workstations require password-protected screen-savers.
Device inventory (Appendix B) is maintained and inspected for tampering or substitution.
Exercise caution with email attachments and links from unknown senders.
5. Protect Stored Data
Best Budz does not store electronic PAN or sensitive authentication data.
Any hard-copy card data is secured and destroyed when no longer needed.
If PAN must be displayed, mask to the first six and last four digits.
Never store magnetic-stripe data, CVV2/CVC2/CID, or PIN/PIN block data.
6. Information Classification
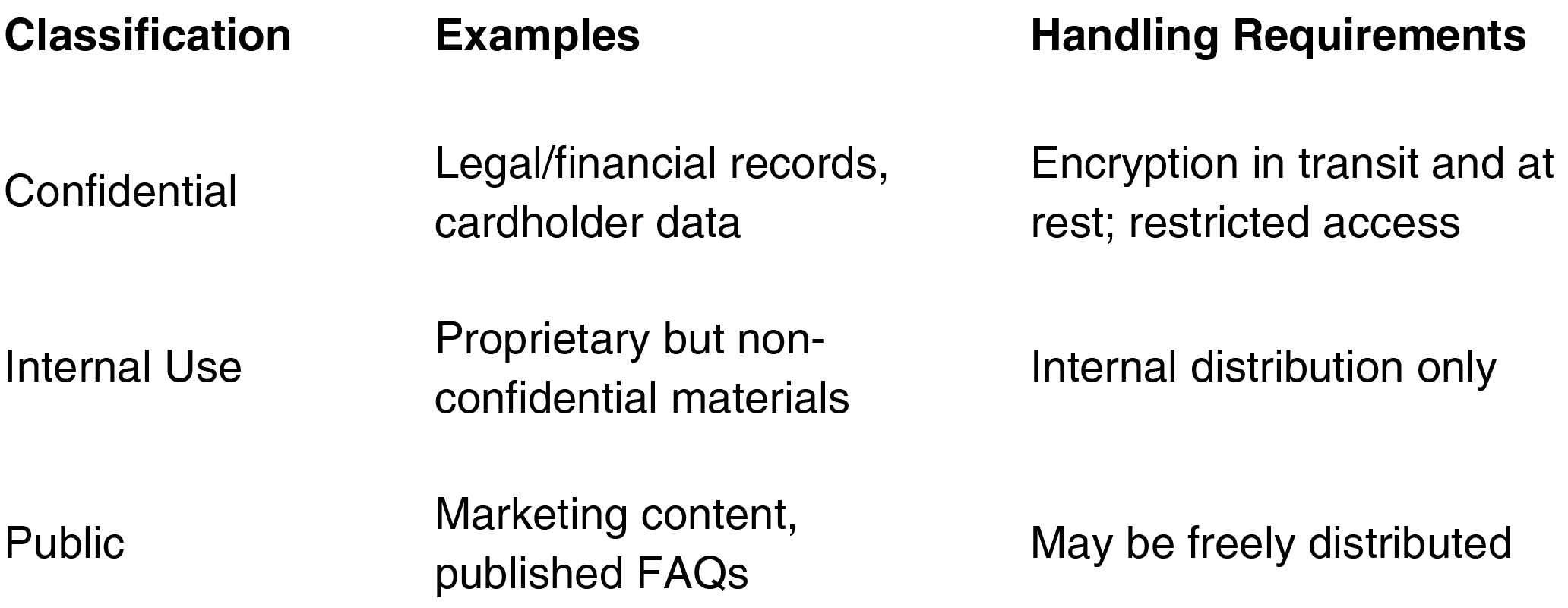
Classification
Confidential
Internal Use
Public
Examples
Legal/financial records, cardholder data
Proprietary but non-confidential materials
Marketing content, published FAQs
Handling Requirements
Encryption in transit and at rest; restricted access
Internal distribution only
May be freely distributed
7. Access to Sensitive Cardholder Data
Access is limited to individuals with a legitimate business need.
Display of PAN is limited to the first six and last four digits.
A list of approved third-party service providers (TPSPs) is maintained (Appendix C).
Due-diligence processes verify each TPSP’s PCI DSS compliance.
8. Physical Security
Media containing sensitive data is stored in physically restricted areas.
Visitors are escorted in secure areas at all times.
POS/POI devices are listed (make, model, location, serial #) and inspected for tampering.
9. Protect Data in Transit
Cardholder data is never sent via clear-text email, chat, or other insecure channels.
Strong encryption (TLS 1.2+, AES, PGP) is required for authorized transmissions.
Physical transport of sensitive media must be logged and handled via secure courier.
10. Disposal of Stored Data
Data is securely destroyed when no longer required.
Electronic media is degaussed or securely wiped.
Paper is cross-cut shredded.
11. Security Awareness and Procedures
Policy is distributed to all personnel; signed acknowledgments are retained.
Background checks are performed within legal limits.
Third parties accessing card data must contractually comply with PCI DSS.
Policies are reviewed at least annually.
12. Credit Card (PCI) Security Incident Response Plan
TP Touch Down Solutions LLC maintains an incident response framework designed to address cardholder data incidents in accordance with PCI DSS. In the event of a suspected or confirmed security breach involving payment data:
The incident will be promptly assessed and investigated by designated personnel or a qualified third-party service provider.
Required notifications will be made to affected card brands and acquiring banks as necessary, following the card brands’ data compromise procedures.
All findings and corrective actions will be documented and retained securely.
While reasonable and industry-standard security measures are maintained to reduce risk, TP Touch Down Solutions LLC cannot guarantee the prevention of unauthorized access or data misuse.
13. Transfer of Sensitive Information Policy
Third-party companies must have SLAs and comply with Best Budz security requirements and PCI DSS.
14. User Access Management
Formal user-registration process; unique IDs issued.
Least-privilege principle enforced.
Accounts disabled immediately upon termination or role change.
15. Access Control Policy
Complex passwords (minimum 8 characters, changed every 90 days).
Privileged access requires dual authorization.
Remote access follows the approved Remote Access Policy and uses MFA.
appendices
Appendix A – Agreement to Comply Form
(Employee acknowledgment form – to be completed and retained.)
Appendix B – List of Devices
(Inventory to be populated and reviewed quarterly.)
Appendix C – List of Third-Party Service Providers
Appendix D – Stand-Alone & P2PE POI Management Policy
Maintain current inventory of all POI devices.
Secure devices with tamper-evident seals or locked enclosures.
Inspect devices at least quarterly; log findings.
Change default passwords and restrict admin access; apply firmware patches promptly.
Restrict physical/logical access to authorized personnel and enforce MFA where possible.
Appendix E – eCommerce Configuration & Hardening Policy
Remove unnecessary services and default accounts.
Enforce TLS 1.2+ for all public-facing services.
Apply OS and application patches within 30 days.
Implement file-integrity monitoring, anti-malware, and endpoint-detection tools.
Limit root/administrator access; enforce MFA; maintain audit logs.
Perform quarterly vulnerability scans and after significant changes; remediate critical findings within 30 days.
Maintain daily off-site backups; test restores annually.
Enable real-time alerting via WAF and IDS; follow the Incident Response Plan for any detected compromise.
For questions regarding this Information Security Policy, please contact the Security Officer via https://bestbudzonline.com/


